From: https://www.us-cert.gov/ncas/alerts/TA17-318A
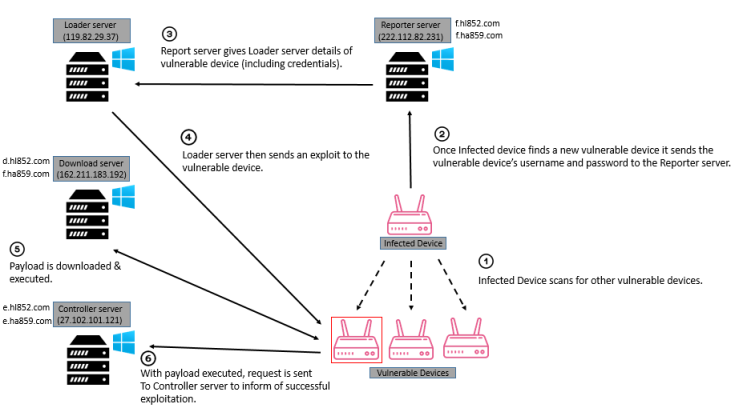
This is an alert by the homeland of security about North Korea malware. The malware called Fallchin has been targeting financial industries and telecommunication since 2016. The hackers can issue commands from a command and control server to the computer that is infected. The way to get infected is by visiting sites compromised by the virus.
North Korea hacking is quite terrifying, since we cant respond with a counter attack. They have nothing to lose right now and they know this hacking will not spark a war. They are one of the only nations that can get away with cyber warfare without much cause for concern. Luckily, we have the department of homeland security cyber professional analyzing threats and alerting us when a threat occurs.




 From: https://github.com/ecthros/uncaptcha
From: https://github.com/ecthros/uncaptcha